Authorization
In this tutorial, we are going to discuss about Authorization. Authorization is the process of determining and granting the appropriate access rights and privileges to an authenticated user or system. It ensures that only those who are allowed to access specific resources and perform certain actions can do so.
Authorization in software systems is like getting a specific wristband at a festival that allows you access to certain areas. It’s about granting or denying permissions to do something after your identity is verified.
Authorization always comes after authentication. First, the system recognizes you (like the club knows who you are), and then it decides what you are allowed to do (like what areas of the club you can enter).

Key Concepts in Authorization
Roles
- These are like different types of wristbands or badges. For example, an ‘Admin’ might have access to everything, while a ‘User’ has limited access.
- Groupings of permissions that can be assigned to users or systems. Roles simplify the management of permissions by aggregating multiple permissions into a single entity.
Permissions
- Specific actions you’re allowed to perform, like viewing, editing, or deleting information. If you’re at a festival, it’s like being allowed to enter backstage areas, VIP sections, or just the general area.
- Specific rights granted to users or systems to perform actions on resources. For example, read, write, execute, or delete permissions.
Policies
- Rules that define how permissions are granted and enforced. Policies can include conditions under which access is granted, such as time of day or IP address.
Importance
- Security: It prevents users from accessing data or actions that they shouldn’t. Like keeping regular festival-goers out of VIP areas.
- Data Integrity: Helps ensure that data isn’t wrongly modified or deleted.
- Compliance: Many industries have regulations about who can access or modify certain data.
Examples
- File System Permissions: Like on your computer, where some files are only accessible by the administrator.
- Database Roles: In a company’s database, different employees have different levels of access based on their job.
- Web Application Privileges: On a website, a regular user might only view content, while an editor can create and edit content, and an administrator can access user data and site settings.
Types of Authorization
- Role-Based Access Control (RBAC):
- Roles: Define a set of permissions that are assigned to users based on their role within an organization.
- Role Hierarchies: Allow roles to inherit permissions from other roles, enabling a structured and scalable way to manage access.
- Attribute-Based Access Control (ABAC):
- Attributes: Uses attributes (such as user roles, resource types, and environmental conditions) to define access policies.
- Dynamic: Offers fine-grained and context-aware access control based on a wide range of attributes.
- Discretionary Access Control (DAC):
- Owner-Based: The owner of a resource has the discretion to set access controls and grant permissions to other users.
- Flexible: Allows resource owners to share resources with others as needed.
- Mandatory Access Control (MAC):
- Policy-Based: Access decisions are based on a set of policies defined by a central authority, rather than by the resource owner.
- High Security: Often used in environments requiring strict control over information, such as military or governmental systems.
- Policy-Based Access Control (PBAC):
- Policies: Uses formalized policies to govern access decisions, which can be based on various factors including roles, attributes, and contextual conditions.
Authorization Mechanisms
- Access Control Lists (ACLs):
- Lists that specify which users or systems are granted access to specific resources and what operations they are allowed to perform.
- Commonly used in file systems and network devices.
- Capabilities:
- Tokens or keys that represent a set of access rights. Users or processes possess capabilities that define their access permissions.
- Often used in distributed systems.
- Role-Based Permissions:
- Permissions are grouped into roles, and users are assigned roles based on their job functions. This simplifies the management of permissions.
- Attribute-Based Policies:
- Policies that use attributes of users, resources, and environmental factors to make dynamic access control decisions.
- Enables fine-grained and flexible access control.
Best Practices for Authorization
- Principle of Least Privilege:
- Grant users only the permissions they need to perform their job functions. This minimizes the potential damage from accidental or malicious actions.
- Role Management:
- Regularly review and update roles and permissions to ensure they reflect current job functions and organizational needs.
- Use role hierarchies to simplify management and enforce consistent access controls.
- Policy Enforcement:
- Implement and enforce policies consistently across the organization. Ensure policies are well-documented and communicated to users.
- Regular Audits:
- Conduct periodic audits of access controls to verify that permissions are appropriate and aligned with security policies.
- Identify and revoke unnecessary or outdated permissions.
- Dynamic and Context-Aware Controls:
- Use dynamic access control mechanisms (such as ABAC) that consider contextual factors like time of day, location, and user behavior.
- Implement adaptive policies that adjust access based on real-time risk assessments.
- Segregation of Duties (SoD):
- Separate critical tasks among different users to reduce the risk of fraud or error. Ensure that no single user has control over all aspects of any critical process.
- User Training and Awareness:
- Educate users about the importance of access controls and how to handle permissions responsibly.
- Promote a culture of security awareness and compliance with access policies.
Authorization is a critical aspect of security that ensures users and systems have appropriate access to resources while minimizing the risk of unauthorized actions. By implementing robust authorization mechanisms and best practices, organizations can protect their assets and maintain the integrity of their operations.
Authorization is about having the right level of access to resources in a software system. It’s crucial for maintaining order and security, much like different access levels are important in a well-organized event or facility.
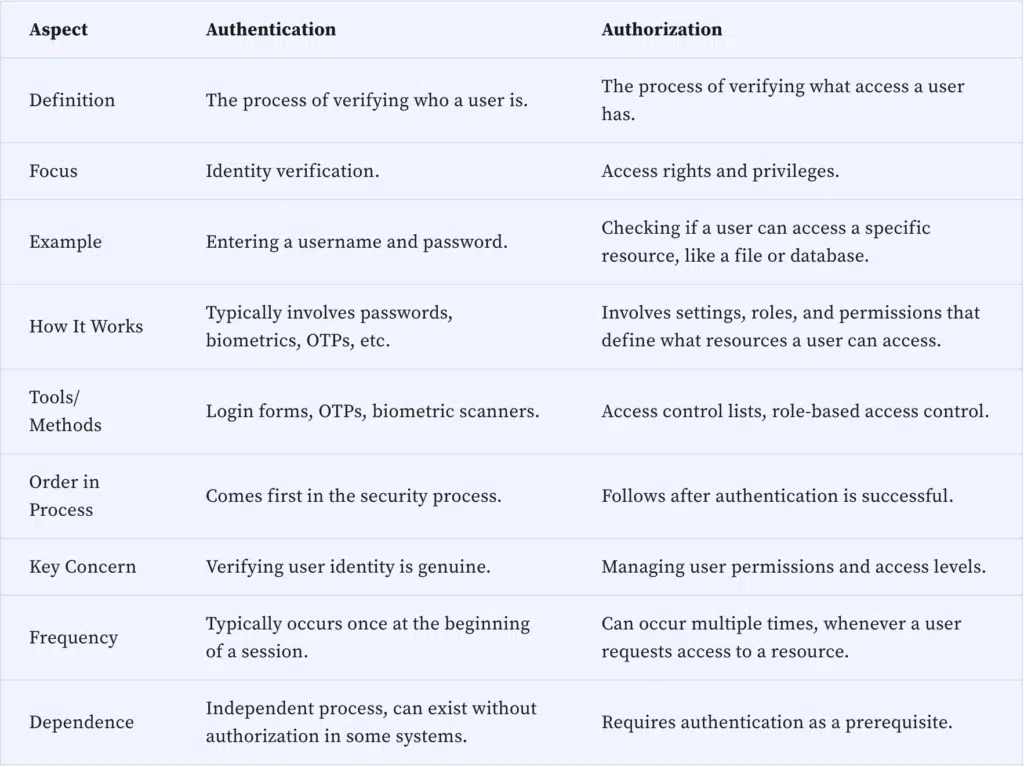
Authentication vs Authorization
Here’s a comparison of authentication and authorization:
That’s all about the Authorization in system design. If you have any queries or feedback, please write us email at contact@waytoeasylearn.com. Enjoy learning, Enjoy system design..!!