Problems With Legacy Systems
In this tutorial, we are going to discuss about the Problems With Legacy Systems. Legacy systems, while often critical to the operations of many organizations, can pose several significant problems. These issues can affect the system’s functionality, performance, security, and maintainability.
What are Legacy System?
Legacy systems are old softwares, technologies, tools, or infrastructures used by an organization. They were often introduced ages ago and might be based on outdated technologies, but they continue to provide essential functions, and that’s why they’ve stuck around.
Different Challenges with Legacy Systems
Here are some common problems associated with legacy systems:
1. Maintenance and Support Challenges
- Obsolete Technologies: Legacy systems often run on outdated hardware and software that are no longer supported by their vendors, making it difficult to find replacement parts or obtain technical support.
- High Maintenance Costs: Keeping an old system operational can be expensive due to the need for specialized skills and custom patches.
- Complexity: Over time, legacy systems can become increasingly complex due to numerous patches, updates, and modifications, making them difficult to understand and maintain.
2. Performance Issues
- Scalability Limitations: Legacy systems are often not designed to scale easily with increased loads, leading to performance bottlenecks as demand grows.
- Inefficiency: Older systems may use inefficient algorithms and processes compared to modern alternatives, resulting in slower performance.
3. Integration Problems
- Incompatibility: Legacy systems can be incompatible with modern technologies, making it difficult to integrate with new applications, systems, or services.
- Data Silos: They often lead to data being siloed within the legacy system, complicating data sharing and collaboration across the organization.
4. Security Risks
- Vulnerabilities: Outdated systems may have known security vulnerabilities that are no longer patched, increasing the risk of cyberattacks.
- Compliance Issues: Legacy systems may not comply with current security standards and regulations, leading to potential legal and financial repercussions.
5. User Experience
- Outdated Interfaces: Legacy systems often have user interfaces that are not intuitive or user-friendly, leading to decreased productivity and user satisfaction.
- Limited Functionality: They may lack modern features and capabilities that users expect, making it difficult to meet current business needs.
6. Business Agility
- Inflexibility: Legacy systems can be rigid and difficult to modify, slowing down the ability to respond to changing business requirements and market conditions.
- Innovation Stagnation: Dependence on outdated systems can stifle innovation and the adoption of new technologies and methodologies.
7. Data Management
- Data Quality: Data stored in legacy systems may suffer from quality issues such as inconsistency, duplication, and inaccuracy.
- Data Migration: Extracting and migrating data from legacy systems to modern platforms can be complex and risky.
8. Operational Risks
- Single Points of Failure: Legacy systems can be critical points of failure in an organization’s IT infrastructure, leading to significant business disruption if they fail.
- Lack of Documentation: Over time, documentation can become outdated or lost, making it difficult for current staff to understand and work with the system.
Why is Replacing Legacy Systems Hard?
- Critical Operations: Many legacy systems are deeply embedded in an organization’s critical operations. Any disruption can have significant impacts.
- Migration Risks: Data migration from old to new systems can be fraught with risks like data loss or corruption.
- Training & Adoption: Staff might be used to the old system. Introducing a new system requires training and can face resistance.
- High Costs: Building a new system and ensuring it works as reliably as the old one can be expensive.
- Unknown Unknowns: There may be undocumented features or behaviors in the legacy system that users have come to rely upon.
Strangler Fig Pattern to the Rescue
Here is how the strangler fig design pattern helps us replacing the legacy system:
- Incremental Replacement: Instead of a big bang approach, replace the legacy system piece by piece. This reduces risks and allows for iterative feedback.
- Coexistence: The new and old systems run side-by-side. As features are moved to the new system, traffic is rerouted accordingly, ensuring operations continue without disruption.
- Feedback Loops: By gradually transitioning users, feedback can be obtained early and often. This ensures the new system meets user needs.
- Reduced Risk: If a part of the new system has issues, it’s easier to revert changes or fix them without affecting the entire system.
- Flexibility: The pattern provides flexibility in adopting new technologies. As the industry evolves, the new system can evolve with it.
- End Goal: Over time, the legacy system’s functionality is entirely replaced by the new system. Once the old system has no more active users or features, it can be safely retired.
Legacy systems pose several challenges related to maintenance, performance, integration, security, and business agility. Addressing these issues requires careful planning and the use of strategic approaches to modernization. By leveraging patterns like the Strangler Fig Pattern, adopting incremental updates, and integrating new technologies, organizations can effectively mitigate the risks and costs associated with legacy systems while paving the way for future growth and innovation.
The Strangler Pattern: A Solution
The implementation of the Strangler Pattern begins by identifying a single functionality of the legacy system that can be rebuilt and redirected to the new system.
Once a functionality is identified, it’s duplicated in the new system, and traffic is rerouted to the new implementation using a Facade interface. This interface is the gatekeeper, directing incoming requests either to the new system or to the old one. Over time, more and more functionality is migrated to the new system, and traffic to the old system decreases until it’s finally phased out.
Steps:
- Identify Entry Points: Choose parts of your legacy system you want to replace and build new services to replace old functionalities.
- Route Traffic: Use a router/proxy to redirect traffic either to the old system or new service, based on what’s been migrated.
- Incrementally Build & Replace: Develop the new microservices and slowly replace old functionalities.
- Retire the Old: Once all functionalities have been taken over by the new system, safely retire the old system.
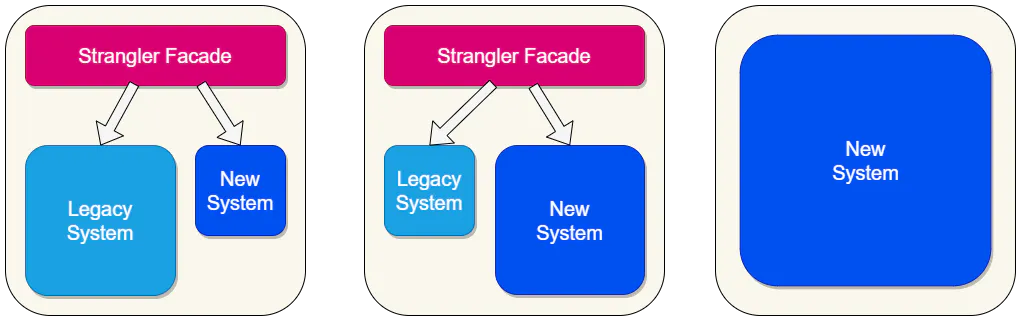
This progressive approach minimizes risk and allows for continuous delivery and integration, making it possible to replace the legacy system without disrupting normal business operations.
That’s all about the Problems With Legacy Systems. If you have any queries or feedback, please write us email at contact@waytoeasylearn.com. Enjoy learning, Enjoy Microservices.!!