Internet and NAT Gateways
In this tutorial, we are going to explore about the Route Tables, Internet and NAT Gateways. These three components play essential roles in controlling network traffic within an AWS Virtual Private Cloud (VPC).
Lets learn how to restrict access to resources inside VPC using route tables, internet gateway, and NAT gateway.
Route tables
Route tables contain a set of rules that serve as guides for directing network traffic within a VPC. They determine where network traffic from our network or gateways should be routed. By default, every VPC is created with a main route table, and each subnet in the VPC is automatically associated with this main route table. The main route table cannot be deleted. However, we can modify its routes.
We do have the option of creating customized route tables for our subnet. One thing to keep in mind here is that we can only attach one route table with one subnet, whereas multiple subnets can be associated with a single route table.

Routes in route tables
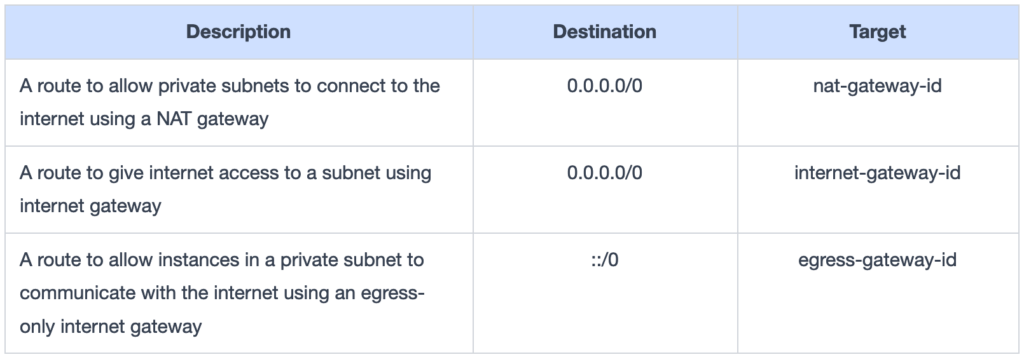
In a route table, a route is a rule that defines how a VPC traffic flows. Each route in a table has a target and a destination. By default, every route table has a local route used for communication within the VPC.
Let’s look at an example of a route table with some sample routes:
Internet gateway
An internet gateway is a component that facilitates communication between instances within a VPC and the internet. It essentially acts as a gateway for internet traffic to and from instances in the VPC. When attached to a VPC, the internet gateway enables instances to connect with resources outside the VPC, such as accessing the internet or communicating with other AWS services outside the VPC.
An internet gateway scales horizontally, is highly available, and doesn’t cause bandwidth constraints for our VPC’s traffic. It facilitates outbound and inbound traffic flows for instances within your VPC.
- Outbound traffic: The internet gateway enables instances within our VPC to communicate with resources and services outside the VPC boundaries, such as accessing websites, downloading updates, or interacting with external APIs. It serves as the conduit through which traffic from our VPC is routed to the internet, allowing the instances to interact with the global network.
- Inbound traffic: With the appropriate security configurations, the internet gateway permits incoming traffic to reach your instances from the internet. This functionality is crucial for hosting services, websites, or applications that need to be publicly accessible. By properly configuring security groups and network access control lists, you can control and manage the types of inbound traffic allowed to reach your instances, enhancing security posture.
Internet gateways don’t give access to the internet by themselves. We must create routes in our route table to allow the subnets in our VPCs to communicate with the internet.
In the diagram below, an EC2 instance in a public subnet is connected to the internet using an internet gateway.

For the use case of our organization, we’ll need to use an internet gateway to allow traffic from the internet to access the frontend components of our application.
NAT Gateway
A NAT (Network Address Translation) gateway is a managed AWS service that enables instances in a private subnet to connect to the internet or other AWS services while preventing the internet from initiating connections with those instances. Each NAT gateway is created in a specific AZ, and allows outbound internet traffic from instances within a private subnet while providing additional security by not exposing the instances’ private IP addresses to the outside world.
When a private instance needs to access the internet, it sends outbound traffic to the NAT gateway. The NAT gateway then translates the private IP addresses of the instances into a public IP address before forwarding the traffic to the internet. Responses from the internet are sent back to the NAT gateway, which then translates the public IP address back into the private IP address of the instance and routes the traffic accordingly.
In the diagram below, we use a NAT gateway to allow an EC2 instance in a private subnet to connect to the internet.

For the use case of our application, we can launch our backend servers in the private subnet and give them access to the internet using the NAT gateway. Through this, traffic from the internet will not be able to access our backend servers.
Connectivity types
When setting up a NAT gateway, we can choose between two connectivity types: public or private.
- Public connectivity type: This is the default connectivity type used by NAT gateways, which enables instances in private subnets to access the internet through a public NAT gateway. However, these instances cannot receive unsolicited inbound connections from the internet. An elastic IP address must be associated with the NAT gateway during its creation in the public connectivity type.
- Private connectivity type: It allows instances in private subnets to connect to other VPCs or on-premises networks through a private NAT gateway. An elastic IP address cannot be associated with the private NAT gateway.
Key points
Some key points related to NAT gateways are given below:
- NAT gateways provide redundancy within the AZ they are created in.
- Rather than associating resources over multiple AZs with a single NAT gateway, we should create multiple NAT gateways in various AZs to improve resiliency in case an Availability Zone is down.
- A NAT gateway can support 5 Gbps of bandwidth by default and can scale up to 100 Gbps if required.
- Security groups can not use a NAT gateway to control inbound and outbound traffic.
- In the case of NAT gateways, we are charged hourly, for each hour our gateway is provisioned and available.
Best Practices
- Route Table Configuration:
- Public Subnets: Route to the IGW for
0.0.0.0/0. - Private Subnets: Route to the NAT Gateway for
0.0.0.0/0.
- Public Subnets: Route to the IGW for
- High Availability for NAT Gateway:
- Deploy NAT Gateways in multiple AZs to ensure resilience.
- Security:
- Use Security Groups and Network ACLs to control access.
- Ensure instances in private subnets do not have public IPs.
- Cost Management:
- Use NAT Gateways judiciously to reduce unnecessary data transfer costs.
That’s all about the Route Tables, Internet and NAT Gateways. If you have any queries or feedback, please write us at contact@waytoeasylearn.com. Enjoy learning, Enjoy AWS Tutorials.!!