AWS PrivateLink and VPC Endpoints
In this tutorial, we are going to explore the AWS PrivateLink and VPC Endpoints and types of endpoints. AWS PrivateLink and VPC Endpoints are AWS networking features that help securely connect services within AWS without exposing traffic to the public internet.
AWS PrivateLink
AWS PrivateLink is a VPC-based service that creates a private connection between VPCs, AWS services and on-premises resources in an AWS Region. Using PrivateLink, we can connect services in one AWS account, different accounts, and AWS partner-supported services. It uses the AWS private network for communication, so the traffic never goes to the public internet. We don’t need a NAT gateway, IGW, or AWS Direct connection to connect to the resources in a private subnet.
Here are some key terms you need to know about when referring to the AWS PrivateLink service:
- Consumer VPC: A VPC in which we want to access a service/application.
- Service provider VPC/ provider VPC/ VPC endpoint service: A VPC hosted in another AWS account that exposes a service/application to be used by the consumer VPC.
VPC endpoints
A VPC Endpoint allows AWS resources in your VPC (Virtual Private Cloud) to connect to AWS services without requiring an Internet Gateway, NAT Gateway, or VPN.
Types of VPC Endpoints
There are two main types:
- Interface Endpoints (AWS PrivateLink)
- Uses Elastic Network Interfaces (ENI) with private IPs in your VPC.
- Supports services like AWS S3, DynamoDB, Lambda, SNS, SQS, etc..
- Allows private communication with AWS services using PrivateLink.
- You must enable DNS resolution to use service-specific endpoints.
- Gateway Endpoints
- Uses a gateway instead of an ENI.
- Supports only Amazon S3 and DynamoDB.
- Requires route table modifications to direct traffic through the gateway.
VPC endpoints are the resources providing the pathway to access the services. There are three types of VPC endpoints, two of which are powered by AWS PrivateLink. The table below shows their main points:

VPC peering vs. AWS PrivateLink
Although both of these services connect resources from different VPCs and allow them to communicate with each other, their use cases and purposes of use are quite different.
- AWS PrivateLink creates a unidirectional connection between the resources of two VPCs. This means that the consumer VPC clients can only initiate the connection.
- VPC peering creates a bidirectional connection between the VPCs. This means that the resources from both VPCs can initiate the communication.
- We need to ensure that the CIDR blocks of IPv4 or IPv6 addresses are not overlapping in VPC peering, AWS PrivateLink uses ENIs, so there is no need to check overlapping.
- VPC peering is cross-regional, but AWS PrivateLink connects resources within the same Region.
Example: Connecting private EC2 instance to SNS
Consider a scenario with an EC2 instance and Amazon SNS. The EC2 instance is provisioned in a private subnet, and we want to connect the EC2 instance with SNS. We have created a NAT gateway in a public subnet, and an internet gateway is attached to the VPC to access the internet. Let’s see different options to access the SNS using the VPC endpoints (Interface).
- Option 1: We use NAT and IGW to access Amazon SNS publicly from the private subnet as shown in the gif below:
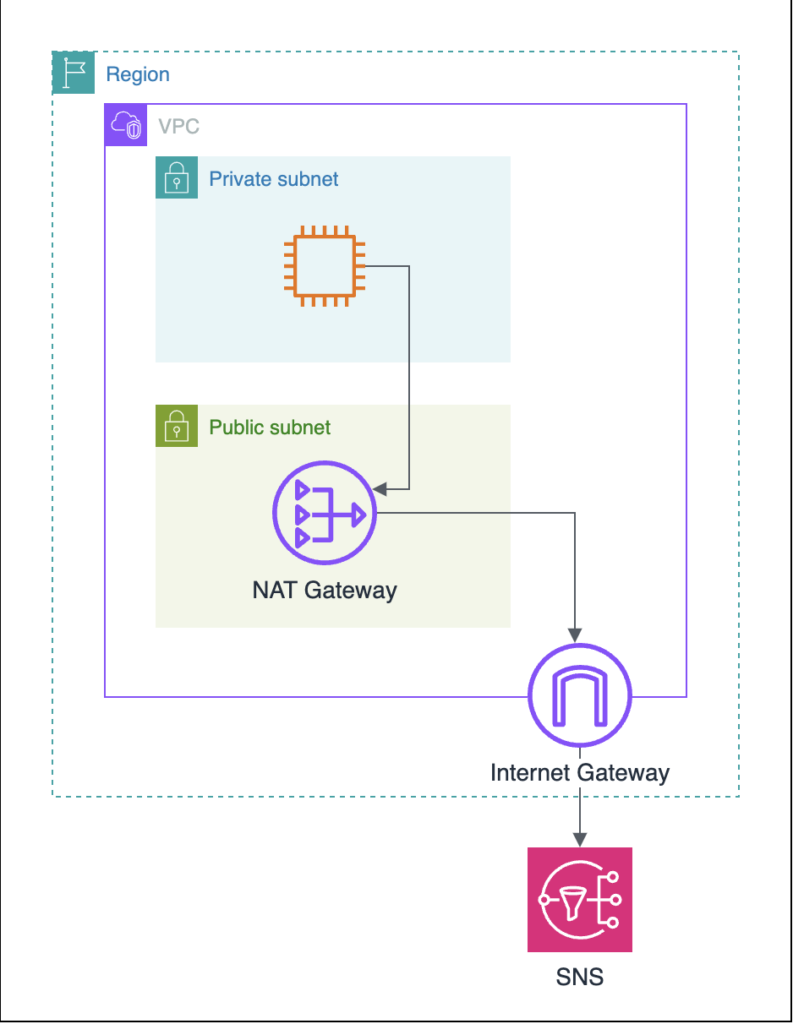
Option 2: We create a VPC endpoint and access Amazon SNS over the AWS private network as shown below:

In option 1, we have to use multiple services (NAT gateway and IGW) to access the Amazon SNS. We can achieve the same in the second option using the VPC endpoint (PrivateLink), and the connection will be private. Also, option 1 is expensive because of the NAT gateway. Therefore, the second option is more suitable and should be adopted.
Important points
Below are a few important points related to AWS PrivateLink and VPC endpoints and they should be kept in mind when working with PrivateLink and endpoints.
- AWS PrivateLink uses private IP addresses to route traffic.
- VPC endpoints allow IPv4 TCP traffic only.
- Almost all AWS services are supported by Interface endpoint (PrivateLink).
- Gateway endpoint currently supports only Amazon S3 and Amazon DynamoDB.
- AWS PrivateLink is not cross-regional.
Summary
- Use a VPC Endpoint if you just need to access AWS services privately.
- Use AWS PrivateLink if you need to expose your own services privately across VPCs, accounts, or SaaS providers.
That’s all about the AWS PrivateLink and VPC Endpoints. If you have any queries or feedback, please write us at contact@waytoeasylearn.com. Enjoy learning, Enjoy AWS Tutorials.!!