Custom VPC and CIDR Block
In this tutorial, we are going to explore about the Custom VPC and CIDR Block. Custom VPC and CIDR Block are the important networking concepts in AWS.
A Custom Virtual Private Cloud (VPC) allows you to define a private network environment for your AWS resources, such as EC2 instances, databases, and containers. A CIDR block (Classless Inter-Domain Routing) defines the range of IP addresses available for the resources within your VPC. Let’s Learn to create a custom VPC and configure IP addresses for subnets to meet the needs of an organization.
A VPC is crucial to deploying and managing resources securely within AWS Regions. We can have a maximum of five VPCs in an AWS Region, including a default one.
Planning IP range for the VPC
Let’s consider an organization with offices worldwide. For now, we are planning connectivity for only one AWS Region, us-east-1. To create our own VPC, we need to take care of the following:
- IP addresses range for the VPC
- Number of availability zones to span the VPC
- Private and public subnets and their IP ranges
When we create a VPC we need to define the CIDR block for our VPC. From the networking point of view, all the resources we create in a VPC must take IP addresses from this CIDR block. Below are a few important points to consider when defining the CIDR block:
- A maximum of five CIDR blocks are allowed per VPC
- A CIDR block can have a minimum size of
/28netmask, allowing for a minimum of 16 IP addresses to a maximum size of/16, accomodating up to 65536 IP addresses. - The CIDR block range for each VPC should be unique and nonoverlapping with each other or our other network.
- The CIDR block must follow the private IPv4 addresses range, as shown in the table below.
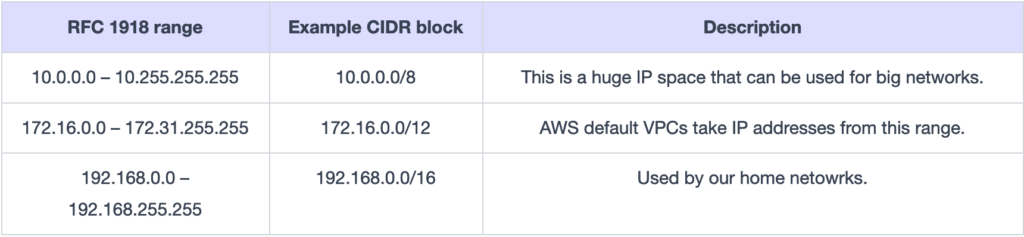
The table above shows the RFC 1918 range for private IPv4 addresses and example CIDR blocks. The AWS default VPCs lie in the IP range of the second row. The 172.17.0.0/16 CIDR block is special because some AWS services like AWS Cloud9 and Amazon SageMaker use it. So, we should avoid assigning the 172.17.0.0/16 CIDR block to our VPC to prevent any IP conflicts.
Now, we know that our private IPv4 address space. Let’s go on to selecting Availability Zones and adding subnets.
Availability Zones for VPC
Availability Zones are physical locations spread across the AWS Region. Each AZ in a region has its own resources independent of other AZs, and together, they create a high-bandwidth and low-latency network. The number of AZs can vary from region to region.
From the VPC point of view, it is important to know the network infrastructure requirements we want to deploy. It helps specify the number of AZs we want our VPC to span. It is recommended to choose at least two AZs for production environments to achieve high availability and fault tolerance. The data transfer across AZs might incur costs. We can go with a single AZ for the testing and development environment to avoid extra costs.
Note: The recommendations above can be changed based on the scenario.
For our use case, the applications of our multi-national organization must be highly available and fault-tolerant, so we’ll select two or three AZs.
Subnets and IP ranges
Subnets are vital components within AWS’s Virtual Private Cloud (VPC), allowing us to deploy our resources carefully and manage the network access effectively.
Types of subnets
Different types of subnets are determined by their routing configurations, which dictate how resources within them connect to the broader network:
- Public subnet: This subnet is connected to an internet gateway, allowing resources within it to access the public internet.
- Private subnet: The private subnet doesn’t have a direct route to the public internet. It requires a NAT device to allow its resources access to the public internet.
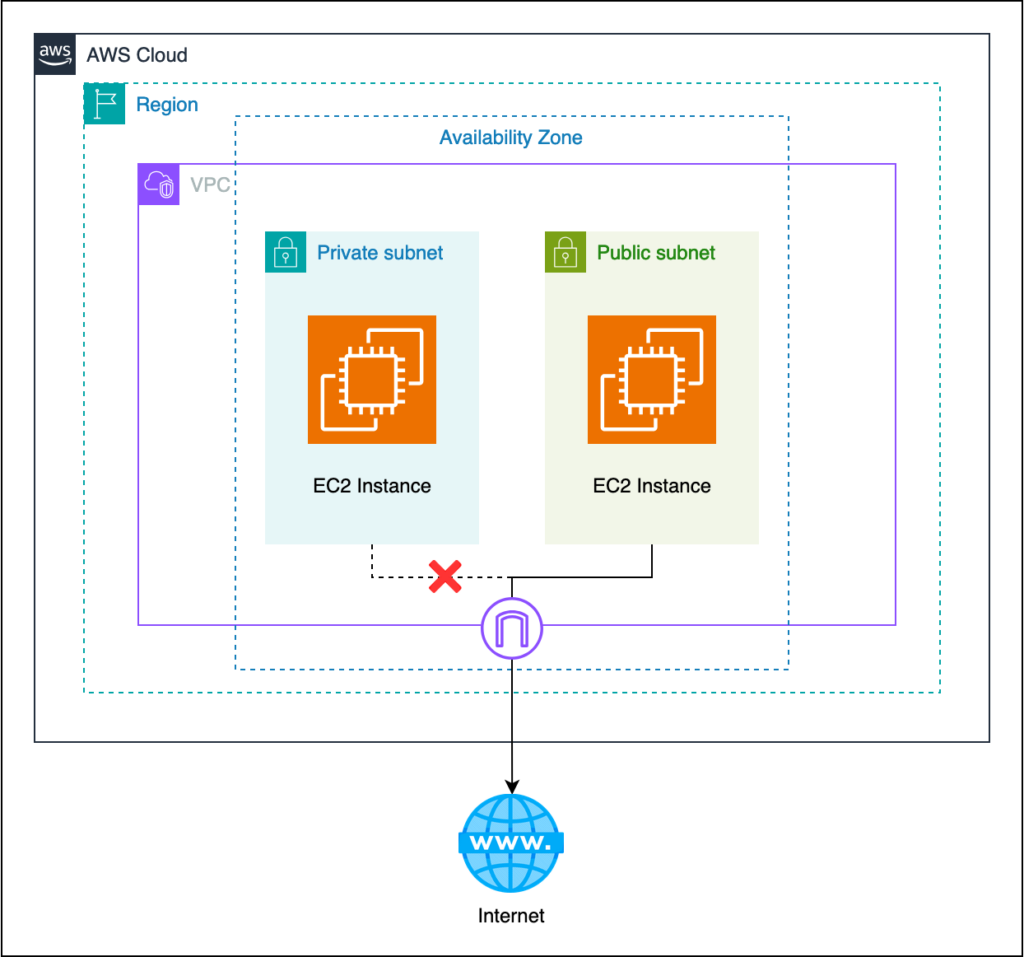
- VPN-only subnet: This subnet routes to a Site-to-Site VPN using a virtual private gateway and does not have a direct route to the public internet.
- Isolated subnet: Subnets of this type have no routes leading to destinations outside their VPC. Resources within an isolated subnet can solely communicate with other resources within the same VPC.
For our use case of a multi-national organization, we might need to select private subnets in one AZ and public subnets in another AZ, depending on the network’s requirements.
IPv4 address range for subnets
When creating a VPC, we allocate a CIDR block to define the overall IP address range for the VPC. Within this range, we reserve specific CIDR blocks for individual subnets. AWS provides flexibility in defining subnet sizes and allows us to allocate appropriate IP address ranges based on the requirements for each subnet. Below are a few important points related to the CIDR block for subnets:
- The CIDR block is only allowed between
/28to/16netmask. - The first four and the last IP addresses in the CIDR range are unavailable and not assigned to instances. The table below, with an example, shows what these IP addresses are used for.

We can use all other IP addresses besides the five mentioned above for our resources.
If we are required to define a subnet with 29 IP addresses available for EC2 instances, then we can’t use
/27netmask because it gives us 32 IP addresses, and after skipping the reserved 5 IPs, we are left with 27, which is < 29. We should create a subnet of size at least/26, which gives us 64 IPs.
That’s all about the Custom VPC and CIDR Block. If you have any queries or feedback, please write us at contact@waytoeasylearn.com. Enjoy learning, Enjoy AWS Tutorials.!!